| |
Timeline 00 - 1600 AD |


 |
3rd cent. Leiden papyrus: medical information gets enciphered to stop abuses
8th cent. - Abu 'Abd al-Rahman al-Khalil ibn Ahmad ibn 'Amr ibn Tammam al Farahidi al-Zadi al Yahmadi finds the solution for a Greek cryptogram by first of all finding out the plaintext behind the encryption, a method which never got out of date. Afterwards he writes a book on cryptography.
- cipher alphabets for magicians are published
1250 the English monk Roger Bacon writes cipher-descriptions. At that time the art of enciphering was a popular game in monasteries
1379 Gabrieli di Lavinde develops the nomenclature-code for Clement VII (114); a code-system made out of ciphers and codes, which kept being irreplaceable until the 19th century
1392 (probably) the English poet Geoffrey Chaucer writes the book The Equatorie of the Planetis, which contains several passages in ciphers made out of letters, digits and symbols
1412 for the first time ciphers including different substitutions for each letter are developed (in Arabic)
~1467 invention of the "Captain Midnight Decoder Badge", the first polyalphabetic cipher (disk); the inventor, Leon Battista Alberti, also called the father of Western cryptography, uses his disk for enciphering and deciphering at the same time
15th/16th century nearly every state, especially England and France, has people working on en- and deciphering for them
1518 the first printed book on cryptology is written by the German monk Johannes Trithemius. He also changes the form of polyalphabetic cipher from disks into rectangulars
1533 the idea to take a pass-phrase as the key for polyalphabetic cipher is realized by Giovan Batista Belaso
1563 Giovanni Battista Porta suggests to use synonyms and misspellings to irritate cryptoanalysts
1585 Blaise de Vigenère has the idea to use former plaintexts or ciphertexts as new keys; he invents the  Vigenère tableau. Vigenère tableau.  David Kahn points out that this technique had been forgotten soon afterwards (until the end of the 19th century) David Kahn points out that this technique had been forgotten soon afterwards (until the end of the 19th century)
1587 Mary, Queen of Scots, is beheaded for the attempt to organize the murder of Queen Elisabeth I., whose agents find out about Mary's plans with the help of decryption
1588 the first book in shorthand is published
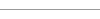
|
|
 |
|
 Vigenère tableau
Vigenère tableau
a b c d e f g h i j k l m n o p q r s t u v w x y z
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Z A B C D E F C H I J K L M N O P Q R S T U V W X Y
source:
 http://www-stud.fht-esslingen.de/projects/krypto/krypt_gesch/krypt_gesch-2.html http://www-stud.fht-esslingen.de/projects/krypto/krypt_gesch/krypt_gesch-2.html
 http://www-stud.fht-esslingen.de/projects/kry... http://www-stud.fht-esslingen.de/projects/kry...
|
|
|